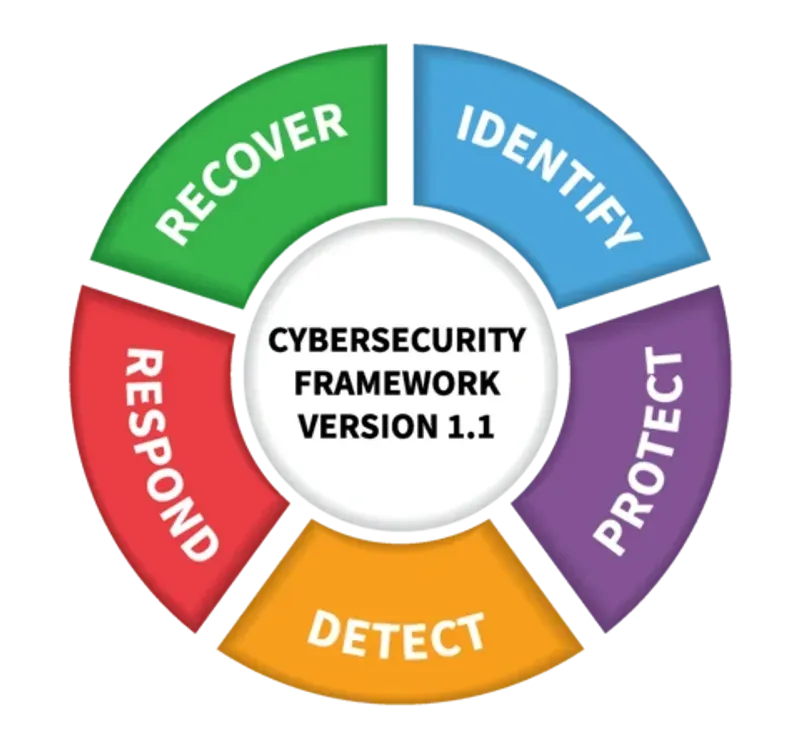
INCIDENT RESPONSE AND MANAGEMENT
RANSOMEWARE AND DATA BREACH
You must view a Ransomware attack as a potential Data Breach. Because ransomware denies access to data, maintaining frequent backups is essential to ensuring the ability to recover data from backups. As the presence of ransomware (or any malware) is considered a security incident under HIPAA, such an attack may result in an impermissible disclosure of Protected Health Information, in violation of the HIPAA Privacy Rule, and may be a breach, depending on the facts and circumstances of the attack.
DETECTION AND IDENTIFICATION
Early detection and identification is key. For your organization, the most challenging part of the incident response process may be accurately detecting and assessing possible incidents, that is, determining whether an incident has occurred and, if so, the type, extent, and magnitude of the problem. Many incidents may be detected by automated detection capabilities, including network-based and host-based intrusion detection systems, antivirus software, and automated log analyzers. Incidents may also be detected through manual means, such as a problem reported by users. Many incidents have overt signs that make them easy to detect, while others are nearly impossible to detect.
QUICK RESPONSE
Once the ransomware is detected, it is your organization’s responsibility to initiate its security incident and response and reporting procedures. We can assist your organization with prioritizing the response to the incident. This is one of the most critical decision points in the incident handling process. We suggest prioritizing based on the functional impact of the incident, the information impacted by the incident, and finally, the time and effort needed to recover from the incident.
CONTAINMENT AND ERADICATION
Containment must occur before an incident overwhelms resources or damage increases or becomes irreparable. A Ransomware attack is type of malware where a malicious process encrypts all the data on the host’s hard drive or network shares. One should not assume that just because a host has been disconnected from the network, further damage to the host or network cannot occur.
Once an incident has been contained, eradication is necessary to eliminate components of the attack, such as deleting malware and disabling breached user accounts, as well as identifying and mitigating all vulnerabilities that were exploited. During eradication, we can assist in identifying all affected hosts so that they can be remediated.
RECOVERY
Recovery is generally phased, and may involve such actions as restoring systems from clean backups, rebuilding systems from scratch, replacing compromised files with clean versions, installing patches, changing passwords, and tightening network perimeter security (e.g., firewall rules, boundary router access control lists).
POST INCIDENT ACTIVITIES
Finally, we can facilitate a“lessons learned” meeting with all involved parties following a major incident. This after action can be useful in improving your security measures and the incident handling process. This meeting provides a chance to learn from the incident, by reviewing what occurred, what was done to intervene, and how well intervention worked.
