Cybersecurity maturity model certification (CMMC): dfars com
WHY IS DFARS CLAUSE 232.204-7012 REQUIRED?
DFARS clause 252.204-7012 was structured to ensure that controlled unclassified DoD information residing on a defense contractor and subcontractor’s internal information system is safeguarded from cyber incidents, and that any consequences associated with the loss of this information are assessed and minimized via the cyber incident reporting and damage assessment processes. This process has been standardized and is now mandatory for DoD suppliers.
WHEN IS COMPLIANCE REQUIRED?
Defense contractors and subcontractors must implement processes whenever covered defense information is processed, stored, or transits through an information system that is owned, or operated by or for, the contractor, or when performance of the contract involves operationally critical support. The requirement is triggered by solicitation/contract for covered defense information or operationally critical support. All covered defense information provided to the defense subcontractor by the Government must be marked or otherwise identified in the contract, task order, or delivery order, and requirements under NIST SP 800-171 must be met.
West Point Security can also assist with Security Policy Review & Development.
IMPLEMENTING NIST 800-171
When you sign a defense contract, whether as a prime or subcontractor, you agree to comply with the terms of the contract, including safeguarding covered defense information. West Point Security has the expertise to provide assistance in determining how your organization can best meet and implement the NIST SP 800-171 requirements in your company.
DEVELOPING A SYSTEM SECURITY PLAN
To meet DFARs requirements, companies should have a detailed system security plan in place. In addition, companies should develop an associated plan of action and milestones (POA/M) to describe how and when any unimplemented security requirements will be met, how any planned mitigations will be implemented, and how and when they will correct deficiencies and reduce or eliminate vulnerabilities in the systems. West Point Security can assist you in developing and implementing a System Security Plan and any associated POA/M.
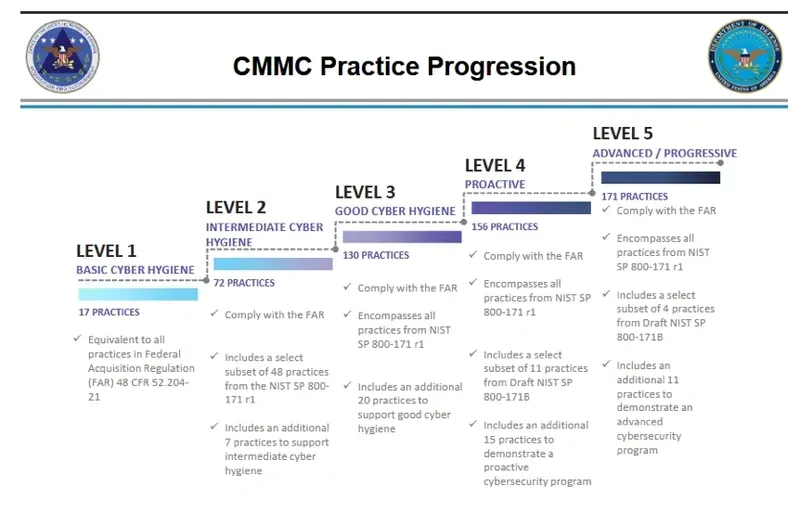
CYBERSECURITY MATURITY MODEL CERTIFICATION (CMMC)
In 2019, the DoD raised the bar when it released the Cybersecurity Maturity Model Certification (CMMC) requirement. With CMMC regulations, there is a new requirement for all 350,000 DoD supply chain members to be certified by an independent third party. Additionally, DoD has determined that CMMC certification costs can be treated as “allowable costs” by contractors.
In addition, certifications will need to be periodically renewed. At the lowest level, certifications are good for three years.
ASSESSMENT LEVELS
DoD methodology consists of three levels of security assessment: (1) Basic Assessment, where a contractor performs a ‘self assessment’ of its System Security Plan developed in accordance with NIST 800-171, resulting in a “low confidence” score. (2) Medium Assessment where the DoD performs a review of the contractor’s System Security Plan, informed by interviews and discussions, resulting in a ‘medium confidence’ score. (3) High Assessment – This is a validation performed by the DoD, consisting of both the DoD’s review of the contractor’s System Security Plan, through interviews and discussions, and an on-site validation of the contractors implementation of these requirements in accordance with NIST 800-171, resulting in a ‘high confidence’ rating.
WEST POINT SECURITY CAN ASSIST IN CMMC CERTIFICATION
Contact us today to start the discussion of how we can assist you in meeting these defense contracting cyber security requirements.
